Cisco Vwlc Keygen DOWNLOAD (Mirror #1). Here is a link for Cisco IOU gen for Python 2. Here is a link for Routing Loop. Bookmark the permalink.
This is a reblog from the original article at Connect IOU with real networks or dynamips
From Internetworkpro
This guide provides explanations to a script called iou2net.pl (script is at the end of the article), which allows you to attach IOU instances to real network (interfaces). In its functionality, its similar to what the ioulive tool does. For more information about IOU or ioulive, ask your Cisco SE/AM that provided you with your copy of IOU, or check out the [IOU FAQ from evilrouters.net][3].
Why another script that does nearly the same thing as ioulive? While playing around with IOU, i tried to come up with a way to attach IOU instances to dynamips directly. I managed to get this working for single instances, but came to the conclusion that its best to integrate such functionality in dynagen directly. Unfortunately, Im not a good programmer and have no experience with python, nor the time to dig through the dynagen sources and extend the code. This script is a byproduct of this work, where i tried to document the packet format that IOU uses to communicate between instances.
Installation
The program is written in perl and can be copied directly from the source listing (end of the article) to a file. Make the file executeable with
Dependencies
iou2net depends on some perl modules. Most of them should come with your default perl distribution. Best case, the extra installation of Net::Pcap should do the trick to satisfy dependencies. On Ubuntu and Debian systems, this is provided with the 'libnet-pcap-perl' package. Of course, beside the perl package, you need libpcap too (not sure if -dev is required).
For systems that dont pack the perl module, use CPAN to install it:
Now try to start the script, it should start without any module warnings, printing the help screen:
Usage
iou2net will forward frames between a IOU instance and a (real) network adapter. IOU needs a special mapping in its NETMAP file. The interface of the IOU instance you want to forward from has to be listed as a source entry, with a '@' suffix at the end. The destination of the mapping will be a pseudo IOU instance number, with a pseudo interface number. iou2net.pl will use this pseudo IOU instance ID to connect to the real IOU instance, and do its frame relaying.
Example NETMAP file:
The first two mappings are normal connections between IOU instances at the same host (R10, 1/1 R11, 1/0 and R10, 1/2 R12, 1/0). The last one connects interface 1/0 of R10 to pseudo router (instance) 20, interface 0/0.
You can choose any ID (<1024), as long as its not used by any real IOU instance. Specify this ID with the option '-p' when launching the script. Dont use this arbitrary ID for anything else in your mappings/topology. iou2net will need to read through this NETMAP file, to determine the correct mapping. By default, it looks in the current directory for the file NETMAP. If you want to use a file in a different directory (and/or with a different name), use the '-n' option. Last, you must specify the network interface where the frames should be forwarded to/received from. iou2net.pl will put this interface into promiscuous mode, therefore you must have superuser privileges when starting the script.
Limitations
- This is only tested with Linux so far. Im sure it will run at other modern Unices, too. From perl perspective, porting this to windows is a possible, yet a pointless approach, because there is no IO_W_ (afaik).
- For the NETMAP mapping line that is related with iou2net.pl pseudo ID, you must use id:x/y interface notation and not the 'compressed' id:z format. Its just a matter of implementation in the script, im too lazy to add this.
- There is not much sanity checking. The last occurence of a line that contains the pseudo ID as a destination is used, no matter how many other mappings with this ID exist before in the NETMAP file. These are typos anyway (see next limitation).
- A single instance of this script will handle one IOU < -> network mapping. If you, for example, have multiple NICs in your systems and therefore want multiple IOU interfaces to be forwarded, you must launch multiple instances of the script. Every mapping must get a unique pseudo ID as the destination, and every instance of the script must be started by adding this unique ID. Example: $ cat NETMAP 10:1/[email protected] 20:0/[email protected] 10:1/[email protected] 21:0/[email protected] 11:1/[email protected] 22:0/[email protected] […]$ sudo ./iou2net.pl -i eth0 -p 20 & […] $ sudo ./iou2net.pl -i eth1 -p 21 & […] $ sudo ./iou2net.pl -i eth2 -p 22 & […]
I didnt test this approach, but it should work. Also, i didnt test the behavior of bridging multiple instances of this script to the same physical interface – please provide feedback.
Run all your IOU instances as the same user, otherwise you end up with different 'netio' subdirectories in /tmp, and your IOU instances cannot talk to each other. The script needs to know the real uid of the user, therefore you should invoke iou2net.pl with sudo, from the same user that runs the IOU instances.
What works
I've done some quick tests with a local IOU instance, one Ethernet interface bridged to a real network where a c1841 is located:
- Basic communication at layer 2 and 3 (Ethernet), up to MTU of 1500
- OSPF adjacency over Broadcast segment (multicast)
- ISIS adjacency
- LDP adjacency
- MPLS encapsulation over Ethernet (@1500 byte [MPLS] MTU, no baby giant/jumbo frame support)
- IPv6 auto discovery
- various connectivity tests toward v4 and v6 Internet
- attaching IOU to dynamips (see below)
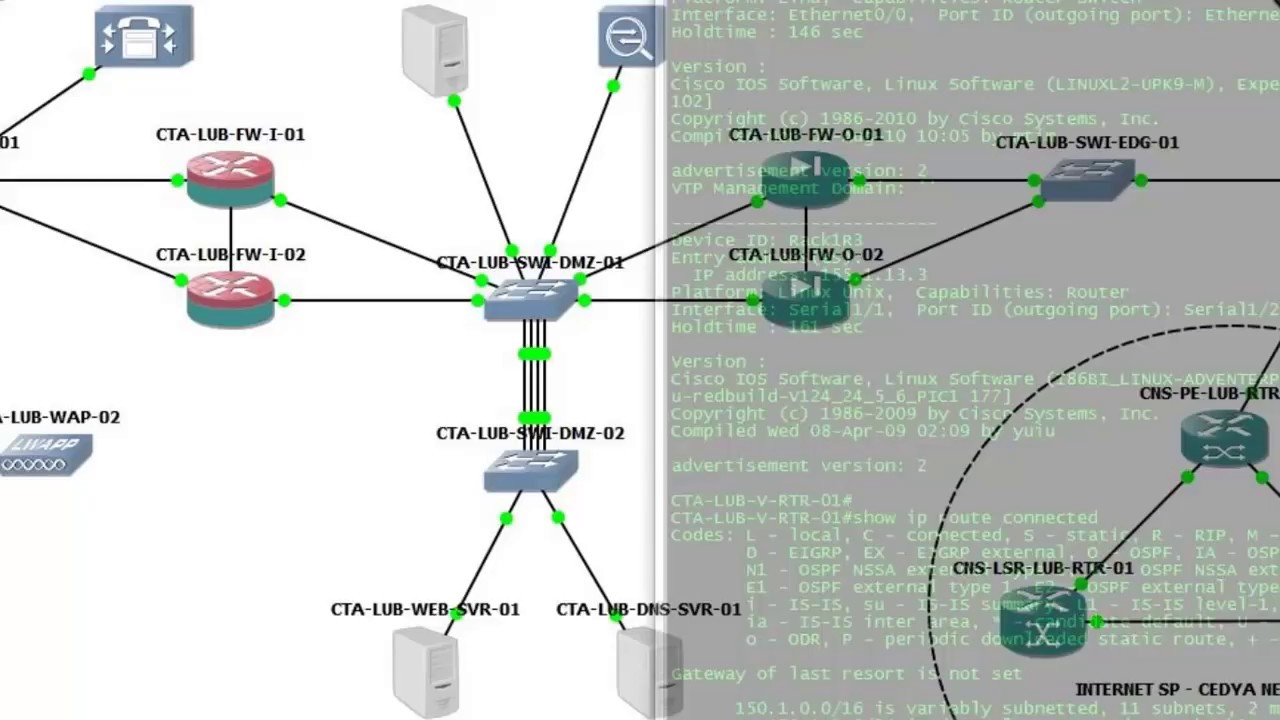
IOU communication
In this cha pter, i will outline the packet format and methods IOU uses when communicating outside of an IOU instance. Inter-instance communication is done through UNIX domain sockets. These are created in the subdirectory '/tmp/netio1000', with a numeric name that corresponds to . So far, i cannot tell whether this directory is the same for anyone, anytime. You can sniff this traffic with strace, like

When sending frames, IOU will submit the entire L2 frame, prepended with a IOU proprietary header. This header is required at the receiving instance, to make the distinction to which local interface the frame is destined to. This is important, because the sockets are per instance (router) and have no way to decide to which internal interface to forward to (whithout extra logic that looks at MAC addresses etc.).
Furthermore, IOU does sanity checks with this header. When receiving a frame, the source information (sending ID, sending interface) is checked against the mappings that were read from the NETMAP file. It is not possible to send frames to an instance with valid destination ID and interface numbers and faked/unknown source information; the source ID and interface numbers have to match also.
The header format is described in the script. I cannot say if the last two bytes are really a delimiter that is always 0x01000, or if these fields serve a different purpose.
The script walks through the NETMAP file and determines the correct mapping, extracts the source IOU instance ID and its interface numbers. As discussed above, this is important for constructing the IOU header. Then it creates a socket $iou_pseudo_sock for out IOU pseudo ID (the destination), the real IOU instance (the source) will send its frames to this socket. This socket will be read- and writeable by anyone, since this script runs as root, where you usually run IOU as a normal user. Furthermore, we bind to the socket of the source IOU instance
($iou_router_sock). The IOU header that is used when sending frames to the real IOU instance is now prebuild, all the required information is available. Next, we bind to the NIC through PCAP routines.
The receiver that handles the traffic direction 'IOU->real network' is forked to allow for non-blocking functionality (There is an option to IO::Socket::UNIX, allowing the socket to operate in nonblocking mode, but i found this way more intuitive). For every frame that the source IOU instance sends, we strip off the first 8 bytes (the IOU header), and transmit the frame via the real NIC.
The receiver that handles the direction 'real network->IOU' is implemented with a pcap capture loop, where the 'logic' is inside the sub recv_loop. Every received frame will be prepended with the precompiled IOU header and send to the socket of the source IOU instance.
This is a reblog from the original article at Connect IOU with real networks or dynamips and probably worth checking there first for any updates.
Other Posts in This Series
- Cisco IOU:Connect IOU with real or external networks (17th April 2011)
- Cisco IOU:Scripted Start Multiple Routing with L2IOU, memory (15th April 2011)
- Cisco IOU: What can Cisco do for Testing, Validation & the IPv6 challenge ? (15th April 2011)
- Cisco IOU: Starting Multiple Routers (15th April 2011)
- Cisco IOU: Shutting down the IOU Processes (15th April 2011)
In our last articles, we learned the beauty of GNS3 to create complex routing labs. However, networks are simply not complete without switches. By now, you should have a few routers (IOS images) in your GNS3 belt. Adding switches is not so easy, but it is definitely doable. In this article, we are going to give you a step-by-step tutorial on how to add Cisco switches to your GNS3 topology.
The GNS3 VM
The GNS3 Virtual Machine is simply a server packed in the form of a virtual machine. Its simple purpose is to run the emulation of your devices in a centralized point: this saves you a lot of resources. In fact, by adding routers with the traditional method of Dynamips, each router eats a lot of RAM and CPU. Well, not anymore with GNS3 VM.
How does it work?
The VM acts as a central point and communicates with your PC through IP on a host-only adapter. Your GNS3 GUI sends a request to the server, which elaborates them and returns replies. As simple as that.
How can we benefit from this?
Trust me, you are going to save tons of computational resources on this. However, this is not all: you add support for L2 devices. Yes, this means you can have a manageable switch in your topology. Once you have this in place, you won't be able to go back to Dynamips anymore.
Installing the GNS3 VM
Getting the VM
The GNS3 VM is free, as GNS3. In fact, it was developed by the same team and you can download it for free from their download page. Ensure to download the VM with the same version of GNS3: in this example, we are using 2.0.3, therefore the VM needs to be that version too. The download link for the VM is quite small, as in the picture below.
At this point, the site will propose several options: VirtualBox, VMWare Workstation, and VMWare ESXi. However, in our last article, we have already used VirtualBox since it is the only free option we have. Therefore, you can simply select VirtualBox. Since this tutorial will show you the steps to do that with VirtualBox, you need to have it installed. In case you haven't, or you are confused about it, just check our latest article about integrating GNS3 with VirtualBox.
This download will give you a compressed file. You can simply un-zip it with our favorite tool (like 7zip), and you will find an OVA file in it.
The OVA
OVA is a special file format that contains Virtual Appliances. Each file contains all the details for a virtual machine: its software, virtual disks, and resource settings. It is like receiving a physical PC with all the needed software already on it. However, this is virtual: much simpler. If you installed VirtualBox correctly, your PC knows that it has to open OVA files with it. As a result, you will see an orange box icon next to the file.
Just double-click on the file to open it. This will open VirtualBox and launch the Import Wizard: a window that looks like the following one.
Here you can check all the settings, and eventually modify some. However, the GNS3 VM was packed this way for a reason. Because of that, you don't need to do anything special here: just click Import. The import will last a few seconds, then you will have to click on Finish. And this is it. Now that we have the GNS3 VM, we need to associate it with GNS3.
Setting-up GNS3
The Local Server
With VirtualBox open, launch GNS3 as an administrator. When starting, GNS3 will raise a pop-up asking to configure a local server: today we are going to do it, and get rid of that pop-up forever. In case your GNS3 doesn't do that, don't panic. Just navigate to the preference and find your way to Server and GNS3 VM. You will be able to follow this tutorial anyway.
Here, be sure that you have selected the first option: Run modern IOS, which should be the default. Then, click Next to move to the following step. At this point, the Wizard will ask you to configure a Local Server. Here, change the Host Binding to 127.0.0.1. This will ensure you will have GNS3 always working, even if you are offline. Click 'next' and GNS3 will try connecting.
In case you receive a failure message, navigate to the path specified in Server path and run gns3server.exe manually by double-clicking on it. Then, click 'Next' again.
The GNS3 VM

The next point in the setup is finally the GNS3 VM. Here, you just have to select VirtualBox. GNS3 will automatically search in your list of Virtual Machines for the right one. In case it has trouble finding it, just hit 'Refresh' and use the drop-down to select the GNS3 VM. Once finished, click 'next'.
Often times, when clicking Next you are going to have a DHCP error like the one below.
If you see this error 'GNS3VM: DHCP must be enabled on VirtualBox host-only network', don't worry. You can continue the setup-with no problem. At this point, you are going to have a recap window, where you can click Finish.
Cisco IOS on Unix (IOU)
IOS on Unix is what we are going to use our VM for. It is a reworked Cisco IOS that runs on top of Unix, as the name says. As a result, we can efficiently run it on our normal CPU, without having to worry about ASIC emulation. In fact, IOU supports both L2 and L3 devices (including switches!). To install that, you need to have the Cisco IOU images: one for L2 and one for L3. This is copyrighted material, thus I can't give it to you. If your company is entitled to that, just use it. In case it isn't, the Internet is full of stuff, you can easily find it by googling. Once you have the IOU image for L2 and L3, continue with the following steps.
Installing IOU
As soon as you finish creating the GNS3 VM, the following window will appear. This is asking you to install a virtual router or appliance and gives you the options to do that.
In case this window doesn't pop-up, don't panic. You can easily install IOU from Edit > Preferences > IOS on UNIX > IOU devices. If that's the case, navigate to this path and click New.
A new window will appear, asking you what to do with the virtual router we are creating. However, the system will give us the only option to use the GNS3 VM, so we can only click Next.
In the next tab, you will have to give the VM a name, select if that's a L2 or L3 device, and load the image. Below, an example of the configuration.
Once you are happy with the settings, simply click Finish. Repeat this step for the L3 machine, of course. If you did this process from Preferences, don't forget to click Apply before clicking OK.
Cisco Iou Keygen Python 1
When sending frames, IOU will submit the entire L2 frame, prepended with a IOU proprietary header. This header is required at the receiving instance, to make the distinction to which local interface the frame is destined to. This is important, because the sockets are per instance (router) and have no way to decide to which internal interface to forward to (whithout extra logic that looks at MAC addresses etc.).
Furthermore, IOU does sanity checks with this header. When receiving a frame, the source information (sending ID, sending interface) is checked against the mappings that were read from the NETMAP file. It is not possible to send frames to an instance with valid destination ID and interface numbers and faked/unknown source information; the source ID and interface numbers have to match also.
The header format is described in the script. I cannot say if the last two bytes are really a delimiter that is always 0x01000, or if these fields serve a different purpose.
The script walks through the NETMAP file and determines the correct mapping, extracts the source IOU instance ID and its interface numbers. As discussed above, this is important for constructing the IOU header. Then it creates a socket $iou_pseudo_sock for out IOU pseudo ID (the destination), the real IOU instance (the source) will send its frames to this socket. This socket will be read- and writeable by anyone, since this script runs as root, where you usually run IOU as a normal user. Furthermore, we bind to the socket of the source IOU instance
($iou_router_sock). The IOU header that is used when sending frames to the real IOU instance is now prebuild, all the required information is available. Next, we bind to the NIC through PCAP routines.
The receiver that handles the traffic direction 'IOU->real network' is forked to allow for non-blocking functionality (There is an option to IO::Socket::UNIX, allowing the socket to operate in nonblocking mode, but i found this way more intuitive). For every frame that the source IOU instance sends, we strip off the first 8 bytes (the IOU header), and transmit the frame via the real NIC.
The receiver that handles the direction 'real network->IOU' is implemented with a pcap capture loop, where the 'logic' is inside the sub recv_loop. Every received frame will be prepended with the precompiled IOU header and send to the socket of the source IOU instance.
This is a reblog from the original article at Connect IOU with real networks or dynamips and probably worth checking there first for any updates.
Other Posts in This Series
- Cisco IOU:Connect IOU with real or external networks (17th April 2011)
- Cisco IOU:Scripted Start Multiple Routing with L2IOU, memory (15th April 2011)
- Cisco IOU: What can Cisco do for Testing, Validation & the IPv6 challenge ? (15th April 2011)
- Cisco IOU: Starting Multiple Routers (15th April 2011)
- Cisco IOU: Shutting down the IOU Processes (15th April 2011)
In our last articles, we learned the beauty of GNS3 to create complex routing labs. However, networks are simply not complete without switches. By now, you should have a few routers (IOS images) in your GNS3 belt. Adding switches is not so easy, but it is definitely doable. In this article, we are going to give you a step-by-step tutorial on how to add Cisco switches to your GNS3 topology.
The GNS3 VM
The GNS3 Virtual Machine is simply a server packed in the form of a virtual machine. Its simple purpose is to run the emulation of your devices in a centralized point: this saves you a lot of resources. In fact, by adding routers with the traditional method of Dynamips, each router eats a lot of RAM and CPU. Well, not anymore with GNS3 VM.
How does it work?
The VM acts as a central point and communicates with your PC through IP on a host-only adapter. Your GNS3 GUI sends a request to the server, which elaborates them and returns replies. As simple as that.
How can we benefit from this?
Trust me, you are going to save tons of computational resources on this. However, this is not all: you add support for L2 devices. Yes, this means you can have a manageable switch in your topology. Once you have this in place, you won't be able to go back to Dynamips anymore.
Installing the GNS3 VM
Getting the VM
The GNS3 VM is free, as GNS3. In fact, it was developed by the same team and you can download it for free from their download page. Ensure to download the VM with the same version of GNS3: in this example, we are using 2.0.3, therefore the VM needs to be that version too. The download link for the VM is quite small, as in the picture below.
At this point, the site will propose several options: VirtualBox, VMWare Workstation, and VMWare ESXi. However, in our last article, we have already used VirtualBox since it is the only free option we have. Therefore, you can simply select VirtualBox. Since this tutorial will show you the steps to do that with VirtualBox, you need to have it installed. In case you haven't, or you are confused about it, just check our latest article about integrating GNS3 with VirtualBox.
This download will give you a compressed file. You can simply un-zip it with our favorite tool (like 7zip), and you will find an OVA file in it.
The OVA
OVA is a special file format that contains Virtual Appliances. Each file contains all the details for a virtual machine: its software, virtual disks, and resource settings. It is like receiving a physical PC with all the needed software already on it. However, this is virtual: much simpler. If you installed VirtualBox correctly, your PC knows that it has to open OVA files with it. As a result, you will see an orange box icon next to the file.
Just double-click on the file to open it. This will open VirtualBox and launch the Import Wizard: a window that looks like the following one.
Here you can check all the settings, and eventually modify some. However, the GNS3 VM was packed this way for a reason. Because of that, you don't need to do anything special here: just click Import. The import will last a few seconds, then you will have to click on Finish. And this is it. Now that we have the GNS3 VM, we need to associate it with GNS3.
Setting-up GNS3
The Local Server
With VirtualBox open, launch GNS3 as an administrator. When starting, GNS3 will raise a pop-up asking to configure a local server: today we are going to do it, and get rid of that pop-up forever. In case your GNS3 doesn't do that, don't panic. Just navigate to the preference and find your way to Server and GNS3 VM. You will be able to follow this tutorial anyway.
Here, be sure that you have selected the first option: Run modern IOS, which should be the default. Then, click Next to move to the following step. At this point, the Wizard will ask you to configure a Local Server. Here, change the Host Binding to 127.0.0.1. This will ensure you will have GNS3 always working, even if you are offline. Click 'next' and GNS3 will try connecting.
In case you receive a failure message, navigate to the path specified in Server path and run gns3server.exe manually by double-clicking on it. Then, click 'Next' again.
The GNS3 VM
The next point in the setup is finally the GNS3 VM. Here, you just have to select VirtualBox. GNS3 will automatically search in your list of Virtual Machines for the right one. In case it has trouble finding it, just hit 'Refresh' and use the drop-down to select the GNS3 VM. Once finished, click 'next'.
Often times, when clicking Next you are going to have a DHCP error like the one below.
If you see this error 'GNS3VM: DHCP must be enabled on VirtualBox host-only network', don't worry. You can continue the setup-with no problem. At this point, you are going to have a recap window, where you can click Finish.
Cisco IOS on Unix (IOU)
IOS on Unix is what we are going to use our VM for. It is a reworked Cisco IOS that runs on top of Unix, as the name says. As a result, we can efficiently run it on our normal CPU, without having to worry about ASIC emulation. In fact, IOU supports both L2 and L3 devices (including switches!). To install that, you need to have the Cisco IOU images: one for L2 and one for L3. This is copyrighted material, thus I can't give it to you. If your company is entitled to that, just use it. In case it isn't, the Internet is full of stuff, you can easily find it by googling. Once you have the IOU image for L2 and L3, continue with the following steps.
Installing IOU
As soon as you finish creating the GNS3 VM, the following window will appear. This is asking you to install a virtual router or appliance and gives you the options to do that.
In case this window doesn't pop-up, don't panic. You can easily install IOU from Edit > Preferences > IOS on UNIX > IOU devices. If that's the case, navigate to this path and click New.
A new window will appear, asking you what to do with the virtual router we are creating. However, the system will give us the only option to use the GNS3 VM, so we can only click Next.
In the next tab, you will have to give the VM a name, select if that's a L2 or L3 device, and load the image. Below, an example of the configuration.
Once you are happy with the settings, simply click Finish. Repeat this step for the L3 machine, of course. If you did this process from Preferences, don't forget to click Apply before clicking OK.
Cisco Iou Keygen Python 1
Adding the IOU License
Cisco Iou L2 Download
Now you need to add the license of your IOU images. If you got them online, chances are the images will come with a license. If not, the Internet is always your friend, you will probably be able to find even something to generate a license. To add the license, you need to navigate to Edit Preferences > IOS on UNIX (not the devices' section). Here you will have a big text box and a Browse button, which you should click.
Now, select the file containing your licenses, click Apply, and then OK. The license will look something like that:
In case you got an old license for gns3-iouvm, simply rename that part to gns3-vm.
Cisco Iou Keygen Python Free
Conclusion
Awesome! If everything went the right way, you now can use IOU images to run L2 and L3 devices. With them, you will be able to do complex CCNP and CCIE labs and boost your career. Try to drag into your project the IOU devices and see how they react, maybe when having multiple of them running.
Cisco Iou Keygen Python Compiler
What are your thoughts about the GNS3 VM and IOU? What labs are you going to build with them? Just let me know in the comments!
